Proof-of-work (PoW), also known as Nakamoto consensus, stands as a decentralized mechanism for achieving consensus within a blockchain network. This method ensures the security of the blockchain by compelling participating nodes to dedicate energy and engage in a competitive process. Their objective? To solve intricate mathematical puzzles that allow them to append blocks to the chain and, consequently, earn rewards.
Moreover, PoW necessitates unanimous agreement among network nodes regarding the accuracy of crucial network elements, including but not limited to account balances and the chronological order of transactions. Notably, Bitcoin boasts the distinction of being the most substantial blockchain utilizing PoW consensus, as measured by its market capitalization.
The mathematical challenges that nodes within the Bitcoin network tackle demand a substantial computational effort. To maintain competitiveness in a PoW ecosystem, miners frequently resort to employing specialized hardware known as application-specific integrated circuits (ASICs). However, even with the utilization of ASICs, the endeavor to gain majority control over the network and orchestrate a 51% attack—thus enabling the validation of illegitimate transactions—mandates an exorbitant level of computational prowess.
However, the advent of quantum computing technologies has sparked concerns regarding the cryptographic foundations of blockchain technology, including Bitcoin. Quantum computers possess the potential to undermine conventional cryptographic methods utilized in Bitcoin’s transaction verification process.
Specifically, quantum computers exhibit the capability to solve intricate mathematical problems—such as discrete logarithms and integer factorization—at an exponentially accelerated pace compared to classical computers. This emergence of quantum computing presents a post-quantum threat to the security of Bitcoin.
Should a quantum computer of sufficient potency materialize, it could compromise the cryptographic integrity of the algorithms underpinning Bitcoin. This could empower malicious entities to execute attacks previously deemed implausible, such as conducting a 51% attack with significantly reduced computational effort than currently required.
What is Post-Quantum Computing?
Post-quantum computing denotes the era that would ensue following the development and deployment of quantum computers capable of solving computational challenges presently deemed insurmountable for classical computers. This encompasses tasks like simulating quantum systems, factoring large numbers, and resolving specific optimization problems.
Quantum computing fundamentally diverges from classical computing, which relies on bits capable of representing either 0 or 1. Conversely, quantum computing employs quantum bits, or qubits. Thanks to the principles of superposition and entanglement, qubits can concurrently represent 0, 1, or both states simultaneously.
The advent of quantum computing presents one of the most significant impending challenges to the functionality and robustness of blockchains and blockchain cryptography.
In the era of post-quantum computing, cryptographic algorithms resistant to quantum attacks will be developed to safeguard sensitive information in a post-quantum environment.
Potential Quantum Attacks on Bitcoin
Cryptography, a branch of mathematics dedicated to securing communication and data, serves as a cornerstone of Proof-of-Work (PoW) cryptocurrencies like Bitcoin (BTC). The Bitcoin blockchain relies on robust cryptographic mechanisms to maintain the trustless, private, and secure nature of its peer-to-peer transactions. However, the emergence of quantum computers introduces the risk of attacks capable of breaching Bitcoin’s cryptographic defenses.
Bitcoin employs asymmetric encryption, also known as public-key cryptography, which utilizes two distinct keys: the public key and the private key. The public key facilitates data encryption or, in the case of Bitcoin, generates a Bitcoin address where funds can be received. Conversely, the private key is employed for decryption or transaction signing. Possession of the private key serves as proof of ownership of the funds and authorizes transactions, ensuring their secure inclusion in the blockchain.
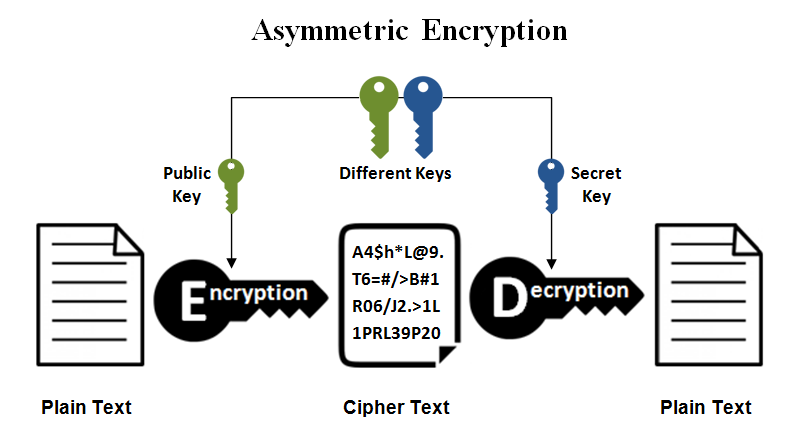
Bitcoin relies heavily on cryptographic techniques, primarily digital signatures and hash functions, which serve as integral components of its security framework. However, the advent of quantum computing poses a significant threat to the effectiveness of these cryptographic mechanisms.
Digital Signatures
The Elliptic Curve Digital Signature Algorithm (ECDSA) is pivotal for verifying Bitcoin ownership and facilitating transaction approval. However, the emergence of powerful quantum computers raises concerns regarding the vulnerability of ECDSA. Techniques such as Shor’s algorithm, theoretically capable of solving the discrete logarithm problem—the cornerstone of ECDSA—in polynomial time, could compromise its security. Quantum computers running the superpositioned Shor’s algorithm could potentially decipher the private key associated with a public key, undermining the integrity of the digital signature.
Hash Functions
Bitcoin relies on cryptographic hash functions like SHA-256 for various purposes, including the mining process and address creation. While hash functions are considered more resistant to quantum attacks compared to public-key cryptography, the threat posed by sufficiently powerful quantum computers remains. Grover’s algorithm, for instance, could accelerate the search for a hash function’s pre-image, albeit at a quadratic speed. Increasing the hash length, such as doubling it from 256 to 512 bits, could mitigate this threat to some extent.
Mitigation Strategies for Post-Quantum Threats in Proof-of-Work Cryptocurrencies
Securing Proof-of-Work (PoW) cryptocurrencies against quantum threats and developing post-quantum blockchain security measures are imperative. Addressing the quantum computing challenge requires the development of solutions capable of safeguarding the blockchain against potential breaches by powerful quantum computers.
Potential approaches include:
Lattice-Based Cryptography
Lattice-based cryptography leverages the complexity of mathematical lattices, which consist of evenly spaced points extending infinitely in all directions. This cryptographic technique employs lattice operations for encryption, decryption, and other cryptographic functions. Deciphering the original message or decryption key without knowledge of the lattice’s precise structure is exceedingly difficult due to the intricate and intractable nature of lattice problems, which form the basis of security.
Isogeny-Based Cryptography
Isogeny-based cryptography represents an evolution of Elliptic Curve Cryptography (ECC), utilizing the mathematical properties of elliptic curves to securely transmit secret messages. However, it introduces additional complexity by leveraging isogenies instead of directly utilizing points on curves, as in traditional ECC.
Isogeny-based cryptography can be likened to two individuals devising a secret handshake in a public setting, where every gesture is observable, yet replication remains elusive. Similar to lattice-based cryptography, its intricate nature provides a potential defense against quantum computer attacks, rendering isogeny-based cryptography a promising avenue for post-quantum cryptographic solutions.
Code-based cryptography operates on the premise of utilizing challenging-to-decode general linear code. This method entails constructing puzzles using error-correcting code, a collection of mathematical tools employed to identify and rectify errors in data transmission. For instance, in the event of data corruption during internet transmission, an error-correcting code would facilitate accurate recovery.
In code-based cryptography, deciphering a message should be straightforward for individuals possessing the appropriate key, yet formidable for others. This cryptographic approach is deemed to possess quantum resistance potential due to the inherent difficulty in decoding random linear code—the fundamental principle of code-based cryptography—using existing algorithms, including Shor’s and Grover’s.
Ongoing endeavors in the realm of post-quantum cryptography are characterized by continuous research and development initiatives. In 2022, the United States Department of Commerce’s National Institute of Standards and Technology (NIST) unveiled the inaugural set of encryption tools specifically designed to withstand assaults from quantum machines. These four selected algorithms are slated to integrate into NIST’s post-quantum cryptographic standard, anticipated to be finalized in 2024.
- CRYSTALS-Kyber, a Cryptographic Suite for Algebraic Lattices, is engineered to serve general encryption purposes, safeguarding connections between web browsers and servers.
- CRYSTALS-Dilithium, another Cryptographic Suite for Algebraic Lattices, is meticulously crafted to supplant existing digital signature schemes like ECDSA.
- SPHINCS+, a stateless hash-based signature scheme, offers an alternative to conventional signature methods, leveraging distinct mathematical problems to ensure security.
- FALCON, or Fast-Fourier Lattice-based Compact Signatures, is tailored for digital signatures based on lattice cryptography. Renowned for its concise signatures and swift verification times, FALCON stands as a testament to efficient cryptographic design.
The prospect of Proof-of-Work (PoW) cryptocurrencies in the quantum era is a subject of profound interest and concern within the cryptographic and blockchain spheres. Researchers from the University of Sussex have projected that a quantum system wielding 13 million qubits could potentially compromise the cryptographic algorithms safeguarding the Bitcoin blockchain within a mere 24-hour window.
Quantum computing poses a potential challenge to the mining aspect of PoW. While techniques like Grover’s algorithm could expedite mining by offering a quadratic speedup in the search for a suitable nonce, the overarching risk to cryptographic security outweighs any potential benefits. However, the requisite processing capacity to substantially influence PoW mining remains beyond current capabilities.
To fortify PoW blockchains against prospective quantum assaults, the blockchain community is actively exploring and devising cryptographic algorithms resilient to quantum threats. Notably, QuEra, a startup spearheaded by former researchers from esteemed institutions like Harvard University and the Massachusetts Institute of Technology (MIT), has unveiled an ambitious roadmap for a forthcoming Quantum machine.
The company envisions the release of a quantum computer boasting 100 logical qubits and 10,000 physical qubits by 2026. This quantum marvel purportedly promises to showcase a “practical quantum advantage,” enabling it to tackle tasks beyond the reach of contemporary bit-based computers.
Despite these advancements, quantum computers still grapple with limitations hindering their ability to crack cryptographic algorithms akin to those utilized in Bitcoin. Factors such as small qubit size and fidelity issues persist as notable hurdles. While the field continues to progress, several technical challenges, including qubit coherence durations and error rates, remain unresolved.
Hopefully, you have enjoyed today’s article. Thanks for reading! Have a fantastic day! Live from the Platinum Crypto Trading Floor.
Earnings Disclaimer: The information you’ll find in this article is for educational purpose only. We make no promise or guarantee of income or earnings. You have to do some work, use your best judgement and perform due diligence before using the information in this article. Your success is still up to you. Nothing in this article is intended to be professional, legal, financial and/or accounting advice. Always seek competent advice from professionals in these matters. If you break the city or other local laws, we will not be held liable for any damages you incur.


